As in our previous topic, we mentioned you about configuring password policy. In this article, I’m going to show you how to configure account lockout policy in Windows server 2016 or previous versions. Account lockout policy is going to work on Windows server 2003, server 2003 R2, server 2008 and server 2012. Also, it can be applied on the local computer as well. Like Windows vista, Windows 7, Windows 8 and Windows 10. First, let me put a glance on account lockout policy and its configuration.
What is Account Lockout Policy?
Account lockout policy disables a user account if an incorrect password is entered a specified number of times over a specified period. These policy settings help you to prevent attackers from guessing users’ passwords, and they decrease the possibility of successful attacks on your network.
So before you enable account lockout policy, it is important to recognize that there is a risk of accidentally locking authorized users out of their accounts. Such a result can be quite costly for your organization because locked-out users cannot access their user accounts until the account unlocks automatically after a specified amount of time or until you unlock the accounts for them.
How to Configure Account Lockout Policy?
To configure account lockout policy read the rest of this article very carefully and do as instructions. First what you are going to do is open up run window and search gpedit.msc then hit enter. Local Group Policy Editor will open up. Now click on Computer Configuration> Windows Settings> Security Settings> Account Policies> Account Lockout Policy. You will see the following options.
- Account lockout duration
- Account lockout threshold
- Reset account lockout counter after
In this topic, we will explain all these options.
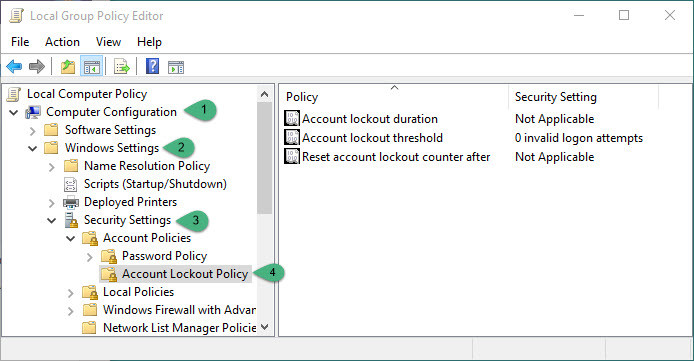
Local Group Policy Editor
#1. Account Lockout Duration
This security setting determines the number of minutes a locked-out account remains locked out before automatically becoming unlocked. The available range is from 0 minutes through 99,999 minutes. If you set the account lockout duration to 0, the account will be locked out until an administrator explicitly unlocks it. If an account lockout threshold is defined, the account lockout duration must be greater than or equal to the reset time. Most the time, when you configure account lockout threshold those two options can be configured. Otherwise, it’s not possible to configure account lockout duration with lockout counter after.
Most the time, when you configure account lockout threshold those two options can be configured. Otherwise, it’s not possible to configure account lockout duration with lockout counter after. By default, this option is set to “None” Because this policy setting only has meaning when an Account lockout threshold is specified.
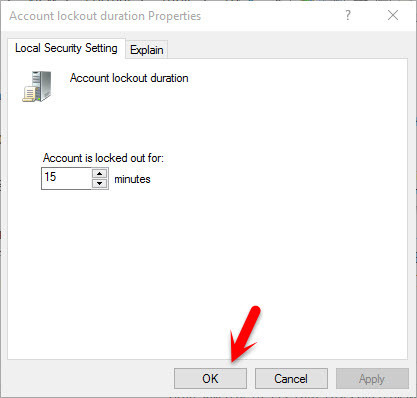
Account Lockout Duration
#2. Account Lockout Threshold
This security setting determines the number of failed logon attempts that causes a user account to be locked out. A locked-out account cannot be used until it is reset by an administrator or until the lockout duration for the account has expired. You can set a value between 0 and 999 failed login attempts. If you set the value to 0, the account will never be locked out. Here I set it to 3. The user can enter the password only for three times. If he enters the incorrect password, his user locks for 15 minutes. You can set up the settings according to your own wish.

Account Lockout Threshold
#3. Reset Account Lockout Counter After
This security setting determines the number of minutes that must elapse after a failed logon attempt before the failed logon attempt counter is reset to 0 bad logon attempts. The available range is 1 minute to 99,999 minutes. If an account lockout threshold is defined, this reset time must be less than or equal to the Account lockout duration. It means that when the 15 minutes complete you can enter the password. If you set it less than 15 minutes, you can enter the password less than 15 minutes.
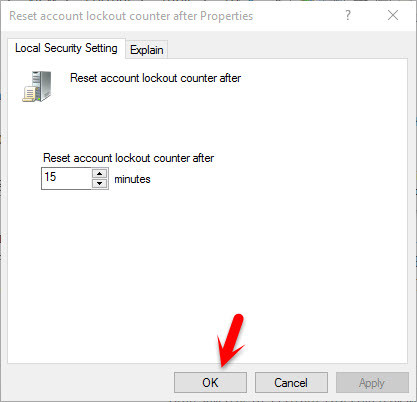
Account Lockout Counter after
Conclusion
If you have got any kind of question in your mind regarding this article feel free to ask us below this post and we will answer it within 24 hours. This was all about how to configure account lockout policy in Windows server 2016 and its previous versions. Thanks for being with us.

hi . i want to set wen user block he need to white 20 minets to unlock . and if he block
2 times in 40 minets . account will be locked out until an administrator explicitly unlocks it when .
thanks for your help
The only possible use we would ever have for a lock-out policy… is 1 that Windows has never supported:
1. Allow an infinite number of guesses.
2. After EACH wrong guess… lock the user out for 3 seconds.
It would be pointless for hackers to waste YEARS trying to guess 1 password.
Valid users would never notice a problem… if they enter a wrong password…
by the time they typed in another one… it would be ok to do so.
They would never notice any “lock out” at all.
Or DOES Windows support that? Perhaps via a direct RegEdit?
Does anyone know the 3 password values that would be needed?
My brother recommended I may lіke this website. He was
once totallу right. This publish truly madе my day.
You cann’t imagine just how much time I had spent for this information! Thank you!
We’re really happy that you found this site helpful.